Over the years I’ve worked in several organisations and most have the same thing in common; over time their access management gets the better of them. Shares grow, more people need access and IT, despite their best efforts, don’t have the knowledge of the business to know who’s access should be removed or added. They fall back on the ITSM service to handle the burden of managing additions and removals and often, spend valuable resource time cleaning the access lists as part of a project or initiative. In other words, IT is responsible for the access management of all shares and their continued security which places a considerable admin overhead on the team.
So here’s a thought; what if the people responsible for controlling access to the data, were the people responsible for the data i.e. the data owner? Taking that one step further, what if anyone can request access to something (e.g. via some sort of self service portal), the request goes to the owner who approves, and the access is then granted, all without the owner needing to put people in groups. In addition, that access could be reviewed on a regular basis, either by the individual, their manager (i.e. does X still require access to Y) or by the data owner?
This is great right? A huge amount of admin overhead is removed from the shoulders of IT and those that own the data are in charge. Lets take that thought process a bit further… What if you could apply this logic to things like SharePoint sites, Teams groups or even licensed applications. What if you could handle the whole joiners/movers/leavers process using this logic?!
Let me introduce Microsoft Entra ID Governance
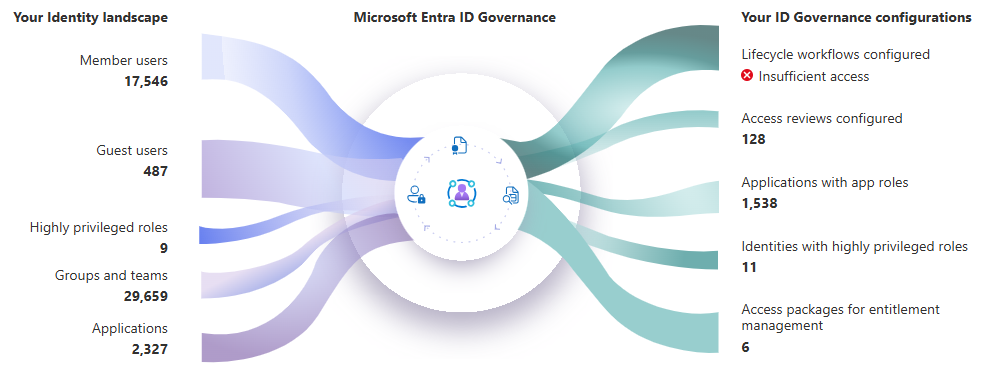
What is Entra Identity Governance?
It’s a set of features in Microsoft Entra that helps you to balance your organisation’s need for security and employee productivity with the right processes and visibility. It allows you to ensure that the right people have the right access to the right resources at the right time. It also helps you to mitigate access risks by protecting, monitoring, and auditing access to critical assets while ensuring employee and business partner productivity.
You can use it to manage the identity and resource access lifecycle at scale, by automating access request workflows, access assignments, reviews, and expiration. You can also use it to periodically review and verify the access rights of your users and groups to ensure that they have the appropriate level of access.
-
Entitlement management: This capability allows you to manage the identity and resource access lifecycle at scale, by automating access request workflows, access assignments, reviews, and expiration. You can use entitlement management to create access packages that define who can request access to which resources, how long the access lasts, and who approves the requests. You can also use entitlement management to enable self-service and delegated access management for your employees, partners, and guests.
-
Access reviews: This capability allows you to periodically review and verify the access rights of your users and groups to ensure that they have the appropriate level of access. You can use access reviews to create scheduled or on-demand reviews for users, groups, applications, or roles. You can also use access reviews to delegate the review tasks to relevant stakeholders or use AI-driven recommendations to make smart decisions.
-
Privileged identity management: This capability allows you to secure and monitor the access of your privileged users and groups who have elevated permissions or roles in your IT environment. You can use privileged identity management to enforce just-in-time and just-enough-access policies for your privileged users and groups, such as requiring multi-factor authentication (MFA), approval, or justification for activating their privileges. You can also use privileged identity management to audit and alert on the activities of your privileged users and groups.
-
Lifecycle workflows: This capability allows you to create custom workflows that perform certain actions based on certain triggers that you define. You can use lifecycle workflows to automate and streamline your identity and access management tasks, such as issuing temporary access passes (TAPs) for new hires, sending notifications or reminders for expiring access, running scripts or commands for specific events, etc.
The Real World
Imagine this scenario:
Harriet is due to start on Monday and will have the role of Service Desk Analyst. To get up and running she will need an account with mailbox, permissions: global reader, Intune Helpdesk Analyst, access to the ServiceDesk Teams group, access to the ServiceDesk wiki site. As these permissions can be a little sensitive, they need to be re-evaluated and a regular basis.
The joiners process can be simple for some roles and more complex for others and request multiple, and often complex processes to enable Harriet to be productive from day one.
Then you also have the movers scenario:
Harriet has been in the business for a while and her manager decides her skills would be better used as an Agile Project Manager. For this role all her existing permissions need to be removed, along with a bunch of apps that were installed on her laptop, and a new set of permissions and apps are required.
So now we have an equally complex scenario where we have to remove old permissions and apps and assign a new set, all without effecting her productivity in either role. Take the old permissions to early and she can’t finishes her old role, give the new permissions to early and she may have access to things she shouldn’t.
Then there’s the ‘..I need access to…’ scenario:
Harriet has been a project manager for a while but now needs to manage a larger, more involved project so she needs access to an existing Teams group and SharePoint site along with some extra apps on her laptop.
This is a common scenario where usually multiple requests need to be made to get up and running i.e. more waiting for fulfilment.
After a few years…
Harriet’s skills have grown over time and unfortunately has been poached by another company. She’ leaving soon and therefore all her permissions need to be removed, the apps removed from her laptop, her OneDrive data shared with manager and her account disabled before being deleted.
Here we have a similar set of issues; take away the apps and permissions too early and she can’t finish all her tasks but leave them in place too long and her identity is at risk.
Cost
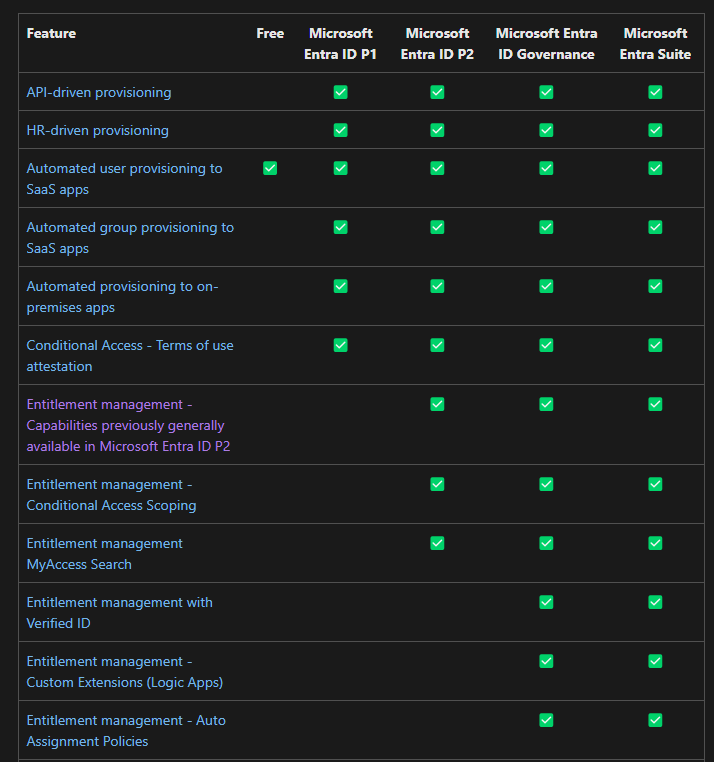
All these scenarios can be handled with Identity Governance but the big question is, what does it cost? Well, as with the majority of MS products it’s a sliding scale - the more you pay, the more features you get. An E3 licence includes Entra ID P1, where as an E5 includes P2. To get all the features you’ll need to buy a full ID Governance license add-on. The full breakdown of what’s included with each license can be found here.
To sum up
So now you know what it is, what it can do and how it can improve common scenarios in your environment. I plan on doing a few more posts where we can dig a little deeper into each of the components and do a walkthrough of how to set them up so come back soon to find out more. Thanks for reading.

